CIS18
Critical Security Controls
Optimize your cybersecurity with CIS18 controls
Gain an overview of your control measures with CIS18—a solution that offers a structured approach to compliance, contributes to ISO 27001, and supports NIS2 requirements.
Build a resilient organization with CIS18
Cyber threats are more advanced than ever and require stronger security measures. With CIS18 controls, you can stay ahead and mitigate even the most complex attacks, ensuring that your organization stands strong against future threats.
RISMA's CIS18 solution protects your organization's critical systems and assets. It provides a complete overview of security controls while documenting how it efficiently supports ISO 27001 and NIS2 compliance—without the need of duplicating efforts.
Prevent business disruption
Ensure that your business operates without interruption, even when cyber threats arise. With a CIS18 solution, you'll protect your company's valuable assets and data to avoid disruption and keep work processes stable and productive.
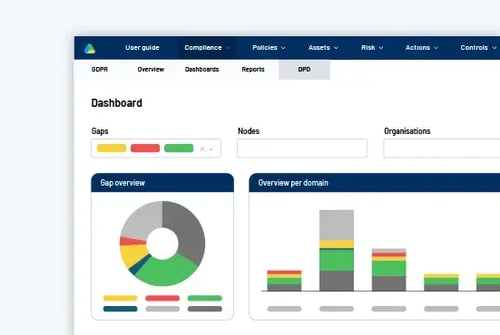
Overview of security controls
Keeping track of all your security controls and ensuring they are adequately implemented can be challenging. RISMA gives you a quick and comprehensive overview of your security controls, including potential security gaps. This way, you can feel confident that your organization is protected against current and future threats.
Efficient CIS18 compliance and risk management
Gain complete insight into CIS18, ISO 27001, and NIS2 compliance and an overview of monthly audit tasks. The solution ensures continuous documentation and makes it easy to follow up, allowing you to identify and address security issues proactively.
Key features of the CIS18 solution
A GRC Platform to bring the organization together
Power your organisation by connecting data, teams, action and reporting in an integrated GRC platform. Whether you deploy one, two, or all our solutions, RISMA GRC platform provides great value by boosting collaboration, increasing visibility, and saving time for everyone involved.
-
Internal audit streamlined
-
Effortlessly automate, document and report all your controls - including assessment, mitigation and monitoring in one simple platform.
-
Risk management organized
-
Define, assess, analyze and mitigate your organization’s risks and turn your insight into strategic assets.
-
Information security systemized
-
Systematize your information security and achieve full ISMS compliance – including visual overview, real-time mentoring, built-in risk assessment and seamless reporting.
FAQ
What are the differences between CIS18 and ISO 27001?
Both CIS18 and ISO 27001 are used to strengthen cybersecurity in organizations and help meet requirements such as NIS2 and DORA, but they have different areas of focus and applications:
- CIS18 is a framework consisting of 18 specific controls and benchmarks designed to protect organizations from cyber threats. It provides a systematic and structured approach to strengthening security measures.
- ISO 27001 is an international standard for an Information Security Management System (ISMS). It focuses on a systematic approach to risk management through policies, processes, and continuous improvements, requiring organizations to establish, implement, and continuously improve their security processes.
While ISO 27001 describes what needs to be done to manage information security at a strategic level, CIS18 offers a more practical how-to approach.
Is CIS18 relevant for my organization?
CIS18 is a voluntary framework that organizations can use to strengthen their cybersecurity and priortize security measures. CIS18 is relevant for both small and medium-sized businesses, big organizations as well as public institutions and infrastructure.
If your organization handles sensitive data, has compliance requirements or seeks to reduce the risk of cyberattacks, CIS18 can be a valuable framework to implement. It's popular because it provides concrete and actionable steps that protect against some of the most common cyber threats.
Does your CIS18 solution support NIS2 compliance efforts?
Yes, our CIS18 solution can be used to support NIS2 compliance efforts.
CIS18 and the NIS2 Directive complement each other and together they can strengthen an organization’s cybersecurity. NIS2 imposes stricter requirements for cybersecurity, preparedness, and reporting, while CIS18 provides a practical and detailed approach to implementing these requirements.
By integrating CIS18 into your security strategy, you can more easily meet NIS2 requirements while simultaneously strengthening overall cybersecurity, making your systems more robust and resilient against cyber threats.
